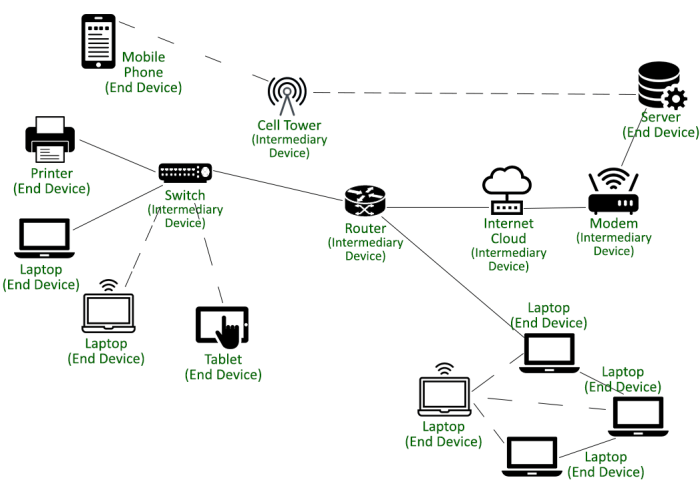
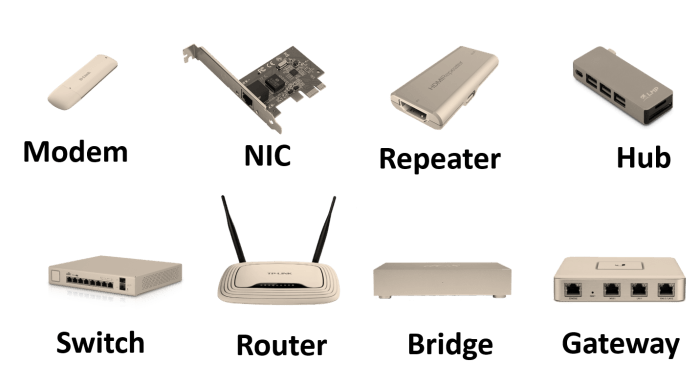
This device connects nodes within the network and hubs – Devices connecting nodes and hubs play a pivotal role in network connectivity, facilitating communication and data exchange within a network. Understanding their functionality, protocols, and management techniques is crucial for optimizing network performance and ensuring its security and reliability.
Network topologies, device functions, and communication protocols lay the foundation for efficient network connectivity. Configuration and management tools enable administrators to fine-tune network settings, while security measures safeguard network integrity from unauthorized access.
1. Network Topology and Connectivity

Devices play a crucial role in establishing connectivity between nodes and hubs within a network. Different network topologies, such as bus, star, ring, and mesh, influence how devices are interconnected and communicate.
Device Interconnection
- Bus Topology: Devices connect to a single shared communication channel.
- Star Topology: Devices connect to a central hub, which manages data transmission.
- Ring Topology: Devices connect in a closed loop, passing data from one to another.
- Mesh Topology: Devices connect to multiple other devices, creating a fully interconnected network.
Impact of Topology
- Bus: Simple and cost-effective, but prone to network congestion.
- Star: Reliable and easy to manage, but can create a single point of failure.
- Ring: Provides redundancy and fault tolerance, but can be more complex to implement.
- Mesh: Offers high reliability and flexibility, but is expensive and complex to manage.
2. Device Functionality and Protocols
Devices perform various functions to facilitate communication and data exchange within a network. They adhere to specific protocols that define the rules and procedures for data transmission.
Device Functions
- Routing: Devices forward data packets along optimal paths to their destinations.
- Switching: Devices connect multiple devices within a network segment, forwarding data based on MAC addresses.
- Bridging: Devices connect different network segments, bridging the gap between different topologies.
- Firewalls: Devices protect networks from unauthorized access and malicious activity.
Communication Protocols
- TCP/IP: A suite of protocols that enables communication between devices on the internet.
- Ethernet: A protocol that defines the physical layer and data link layer for wired networks.
- Wi-Fi: A protocol that enables wireless communication between devices.
- Zigbee: A protocol designed for low-power wireless networks, commonly used in IoT applications.
3. Network Management and Configuration
Network management and configuration are essential for optimizing network performance and ensuring reliable connectivity. Various tools and techniques are employed for this purpose.
Configuration
- Device Configuration: Devices are configured with IP addresses, network settings, and security parameters.
- Network Configuration: Network parameters such as routing tables, VLANs, and QoS settings are configured.
Management, This device connects nodes within the network and hubs
- Network Monitoring: Tools are used to monitor network performance, identify potential issues, and gather data for analysis.
- Troubleshooting: Techniques are employed to diagnose and resolve network problems.
- Network Security Management: Measures are implemented to protect networks from unauthorized access and cyber threats.
4. Security and Access Control: This Device Connects Nodes Within The Network And Hubs
Security is a paramount concern in network connectivity. Devices play a crucial role in protecting networks from unauthorized access and maintaining data integrity.
Security Considerations
- Unauthorized Access: Devices must prevent unauthorized users from accessing the network.
- Data Confidentiality: Data transmitted over the network must be protected from eavesdropping.
- Data Integrity: Data must be protected from unauthorized modification or corruption.
Security Measures
- Encryption: Data is encrypted to prevent unauthorized access.
- Authentication: Users are authenticated before being granted access to the network.
- Access Control: Access to network resources is restricted based on user roles and permissions.
- Firewalls: Firewalls block unauthorized access to the network and protect against cyber threats.
5. Performance and Optimization

Network performance is crucial for efficient data transmission and user satisfaction. Various factors affect performance, and optimization strategies can be implemented to improve it.
Performance Factors
- Network Latency: The time it takes for data to travel from one point to another.
- Bandwidth: The amount of data that can be transmitted over a network connection.
- Packet Loss: The percentage of data packets that are lost during transmission.
Optimization Strategies
- Network Segmentation: Dividing the network into smaller segments to reduce congestion and improve performance.
- Load Balancing: Distributing network traffic across multiple devices to avoid overloading.
- QoS (Quality of Service): Prioritizing certain types of traffic to ensure smooth delivery of critical applications.
6. Case Studies and Real-World Applications
Case studies and real-world applications provide valuable insights into how devices have been successfully deployed to connect nodes and hubs in various scenarios.
Case Study: Enterprise Network
A large enterprise implemented a mesh network to connect its multiple buildings and ensure reliable communication between its thousands of employees. The mesh topology provided redundancy and fault tolerance, ensuring minimal downtime and seamless connectivity.
Case Study: Smart City
A smart city deployed a network of IoT devices to connect traffic sensors, streetlights, and other infrastructure. The devices collected and transmitted data to a central hub, which enabled real-time monitoring and control of city operations, leading to improved traffic flow and energy efficiency.
Essential FAQs
What is the primary function of devices connecting nodes and hubs?
To facilitate communication and data exchange between nodes and hubs within a network, ensuring seamless connectivity.
How do network topologies impact device connectivity?
Different network topologies, such as star, bus, and ring, determine the physical arrangement of devices and influence their connectivity patterns.
What protocols are commonly used for communication between devices?
Protocols like TCP/IP, UDP, and Ethernet define the rules and formats for data transmission, ensuring compatibility and interoperability between devices.